Cyber Warning WannaCry Trojan
Several media and organizations, including Europol, are reporting a large jumber of infections with the ransomware Wannacry that creates havoc since last Friday. Although not spread by email, as far as we know by now, MX Lab wants to inform its blog readers as well.
According to estimations, over 200.000 computers in more than 150 countries are infected with this ransomware. In a lot of cases, more businesses and organizations seems to be among the victims including large corporations. Hospitals, energy producing company in Spain, universities in Britain, ministries, German rail road company,… just to name a few.
The good news is that investigators have found a ‘kill switch’ in the code of the ransomware. The malicious code will check for a certain domain name: IuqErfSodp9IfJapOsdfjHgOsuRijfAewRwErgWea.com.
Since this domain has been registered, the malware stopped encrypting files or its spread is slowed down but researchers warn for new variants where the kill switch is modified or even removed. On Saturday new variants have been reported so it might be possible that during the next few days more variants may appear.
What Wannacry does and what ransomware is
This trojan will use an unpatched and vulnerable Windows operating system to install itself on the target computer and will encrypt important files. The ransomware exploits a vulnerability in SMB server. The trojan has the capability to spread itself over the network without any human interaction like clicking on a link.
Once those files are encrypted, access to those files is impossible unless some money is payed as a ransom. Most of the time, the ransom in payed in bitcoins and the amount can vary from case to case.
What files are affected
The following files may targeted by the Wannacry trojan and become encrypted:
.123, .3dm, .3ds, .3g2, .3gp, .602, .7z, .aes, .ai, .ARC, .asc, .asf, .asp, .avi, .backup, .bak, .bmp, .brd, .c, .cgm, .class, .cpp, .crt, .cs, .csr, .csv, .db, .dbf, .dch, .dif, .dip, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .edb, .eml, .fla, .flv, .frm, .gif, .gpg, .gz, .hwp, .ibd, .jar, .java, .jpeg, .jpg, .js, .jsp, .key, .lay, .lay6, .ldf, .m3u, .m4u, .max, .mdb, .mdf, .mid, .mkv, .mml, .mov, .mp3, .mp4, .mpeg, .mpg, .msg, .myd, .myi, .n, .nef, .odb, .odg, .odp, .ods, .odt, .ost, .otg, .otp, .ots, .ott, .p12, .PAQ, .pas, .pdf, .pem, .php, .pl, .png, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .psd, .pst, .rar, .raw, .rb, .rtf, .sch, .sh, .sin, .slk, .sql, .sqlite3, .sqlitedb, .stc, .std, .stw, .suo, .swf, .sxc, .sxd, .sxm, .sxw, .tar, .tarbz2, .tbk, .tgz, .tif, .tiff, .txt, .uop, .uot, .vb, .vdi, .vmdk, .vmx, .vob, .vsd, .vsdx, .wav, .wb2, .wk1, .wks, .wma, .wmv, .xlc, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .zip.
How to detect that Wannacry has infected my system
- Files that are encrypted by the ransomware will receive the new file extension .wnry, .wcry, .wncry or .wncryt.
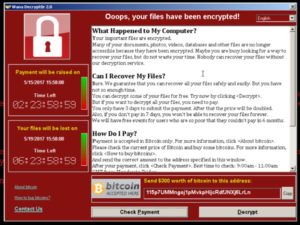
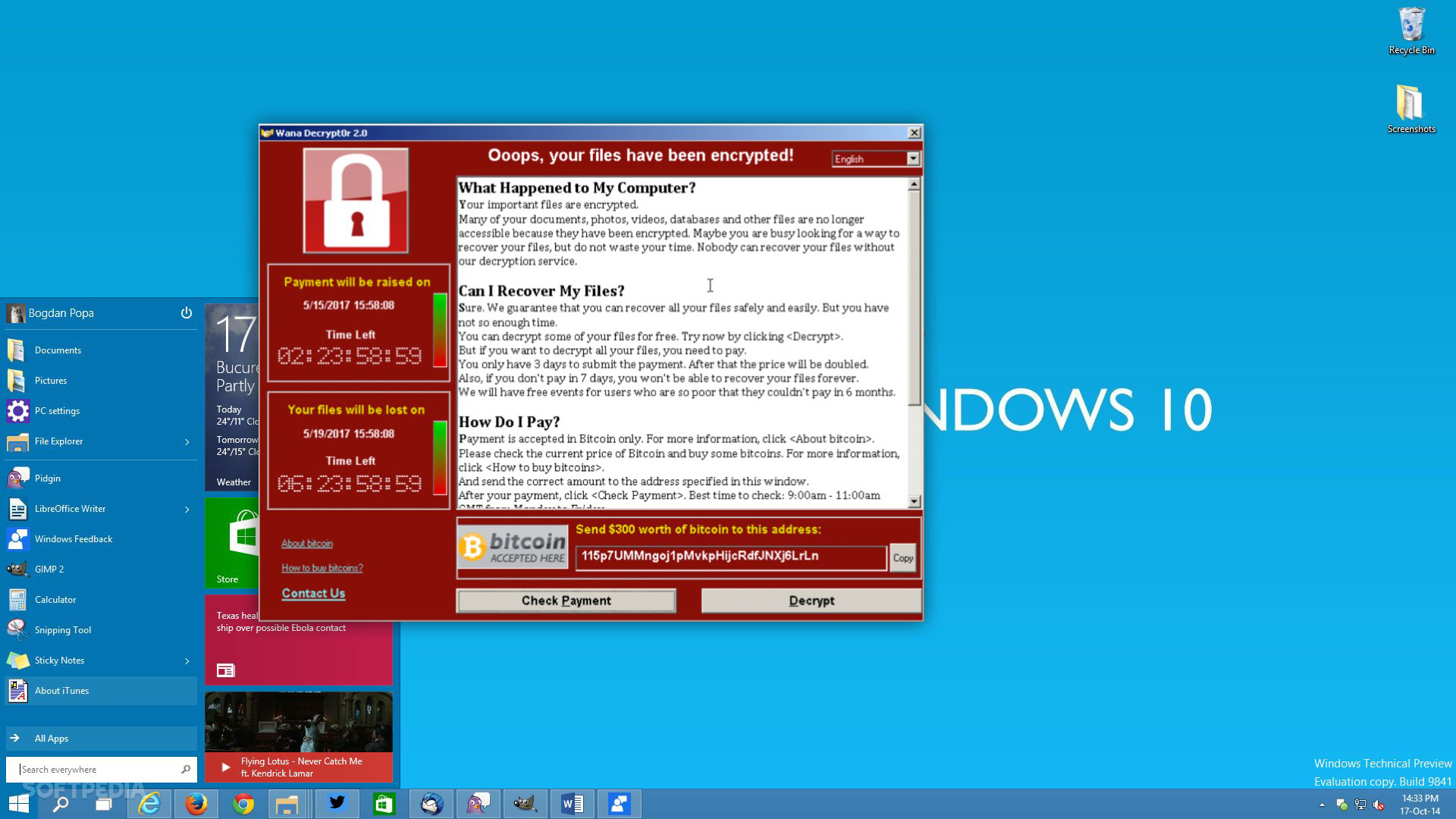
- Furthermore, a screen will pop up (image see below) with the message that your files are encrypted. This message will include information on what happened, an option to decrypt your files but be aware. Your files are not being decrypted unless you pay a certain amount as ransom.
- After a restart you might have a blue screen and you will be unable to continue booting the computer.
My files are encrypted. Should I pay the ransom?
No, it is not recommended to pay the ransom for several reasons:
- You have no guarantee that your files are actually going to be decrypted by the ransomware
- It might be possible that after the first payment, a second payment will be asked, perhaps with an even higher amount.
- By paying the ransomware, the ‘author’ of the ransomware will receive financial aid to fund further malware campaigns.
This might seems to be the easiest solution to get your files back but there is absolutely no guarantee.
It might be better to consider the following options depending on your IT structure and set up:
- Isolate the infected systems and detach from the local network to prevent further spreading
- Clean up the infected system from the ransomware (prefere to start from a clean install or restore point)
- Restore files from backup sources locally or from the cloud
- Ensure all patches are applied before reconnecting back to the network
How to prevent an infection with the Wannacry trojan
- Install the latest Windows patches:
- Windows systems
- Unsupported Windows systems like Windows XP
- Block firewall ports 139, 445 & 3389
- Disable the SMB protocol on system that don’t require it
Ransomware can also be spread by email. MX Lab always recommend to keep an eye out for suspicious emails, especially when attachments, as compressed archives or not, or URLs are embedded. Strange from address, poor formatting and language, very short email body, senders address doesn’t match,.. can all be indications that the email may pose a potential risk.
Further information
Find hereby some web sites with additional information regarding the Wannacry ransomware:
McAfee
Trendmicro Blog
SecureList
Symantec Blog
From MXLab.